P2P Technology Deep Dive: Understanding IPv4, NAT, and Peer-to-Peer Communication
🚀 Introduction to P2P Technology
When developing IP camera streaming applications for mobile devices, I initially struggled with P2P concepts due to my lack of 3D graphics and network communication background. This article represents my deep dive into P2P technology research and serves as the first in a comprehensive series covering complete P2P technology and principles.
What You’ll Learn:
- 🌐 Network architecture fundamentals behind P2P communication
- 🔧 NAT traversal techniques for direct device connections
- 📱 IoT device communication without central servers
- 🎯 Real-world applications in IP cameras and mobile apps
🎯 Why P2P Technology Matters
Before diving into P2P traversal or hole-punching techniques, it’s crucial to understand the problems they solve. P2P enables direct device-to-device connections without relying on central servers, which is critical for IoT devices, AR/VR systems, and self-hosted applications.
Key Benefits of P2P:
- ⚡ Reduced latency - Direct connections bypass server routing
- 💰 Lower costs - No server infrastructure required
- 🔒 Enhanced privacy - Data doesn’t pass through third-party servers
- 📈 Better scalability - No server bottlenecks
- 🛡️ Improved reliability - No single point of failure
🏗️ Network Architecture Types: Centralized vs Decentralized vs Distributed
Understanding these three fundamental network architectures is essential for choosing the right approach for your application.
1. Centralized Networks
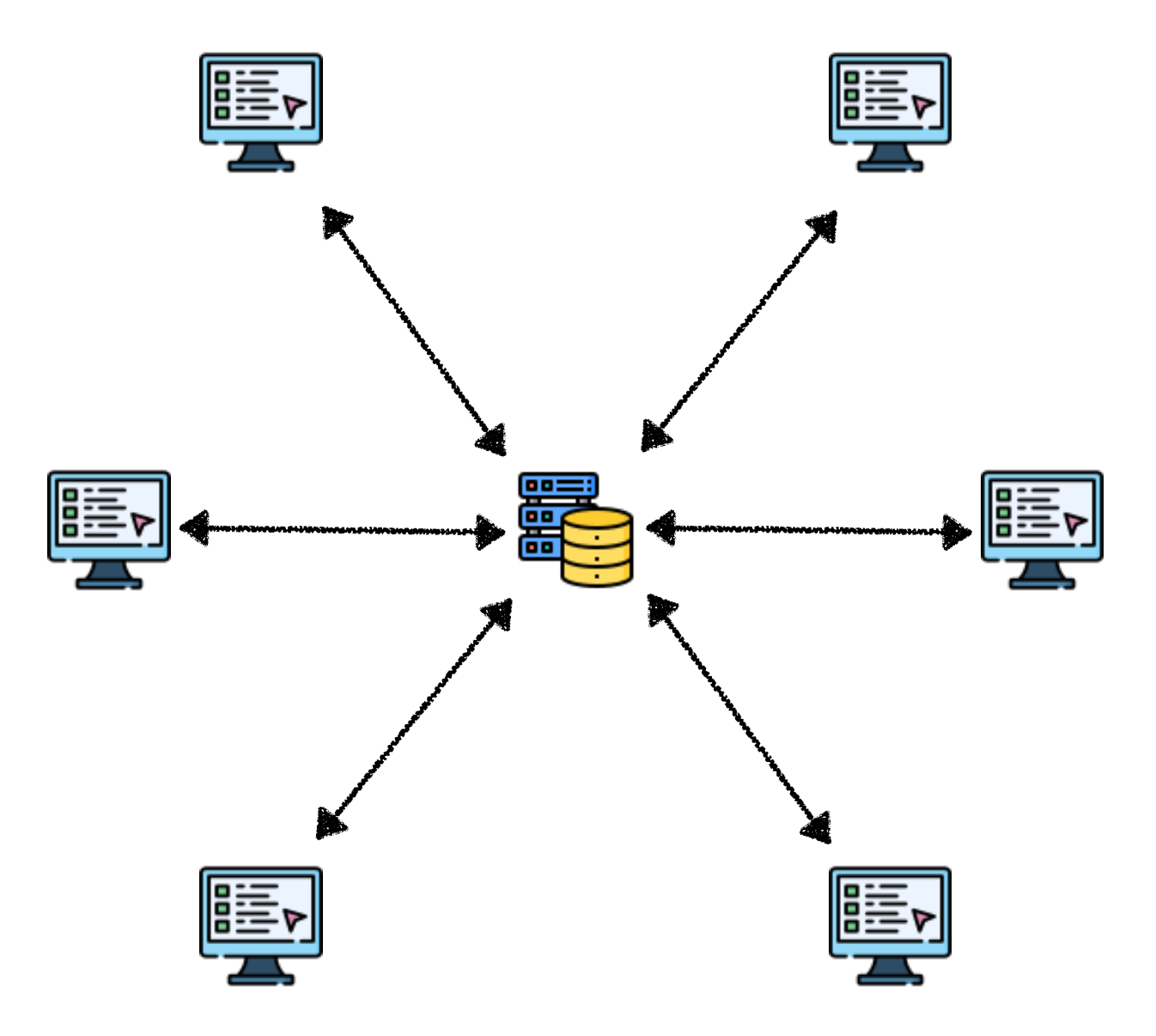
All clients connect to a single server that manages and distributes messages. Think of it like a central bank issuing currency - everyone gets money from the central bank.
Advantages:
- ✅ Simple deployment and maintenance
- ✅ Centralized data management
- ✅ Easy to implement and debug
Disadvantages:
- ❌ Single point of failure
- ❌ Privacy concerns
- ❌ Latency limited by server location
- ❌ Scalability bottlenecks
2. Decentralized Networks
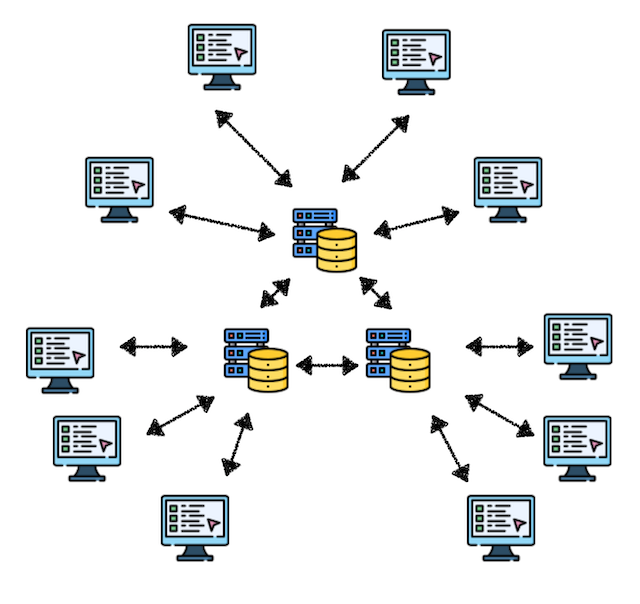
Multiple servers share data, and clients can retrieve information from any server.
Advantages:
- ✅ Higher fault tolerance
- ✅ Better performance flexibility
- ✅ Reduced single point of failure
Disadvantages:
- ❌ Complex system design
- ❌ Higher operational costs
- ❌ Security risks still present
3. Distributed Networks
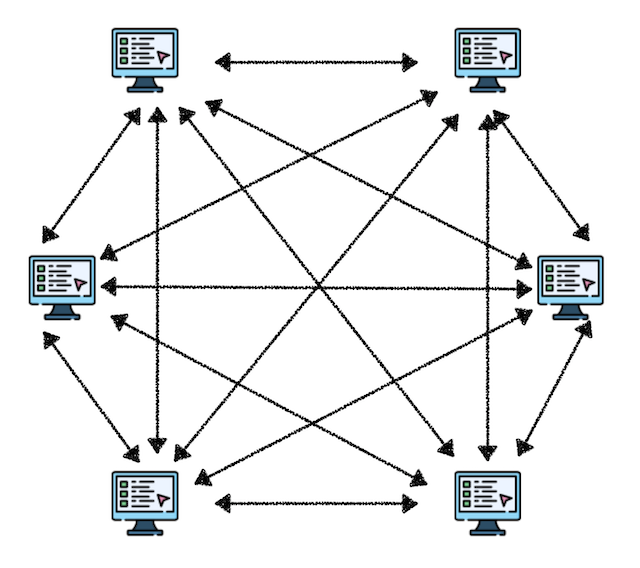
The most evolved form of decentralization - no central servers, with each node capable of sharing and validating data.
Example: Blockchain technology, where each node has complete information without trusting central institutions
Advantages:
- ✅ High fault tolerance
- ✅ Transparency and security
- ✅ Cost savings
- ✅ No central authority
Disadvantages:
- ❌ Complex system architecture
- ❌ Challenging deployment
- ❌ Need to consider device differences
📱 IoT Control Scenarios Comparison
Let’s examine real-world applications using IP camera control as an example.
Centralized Control Approach
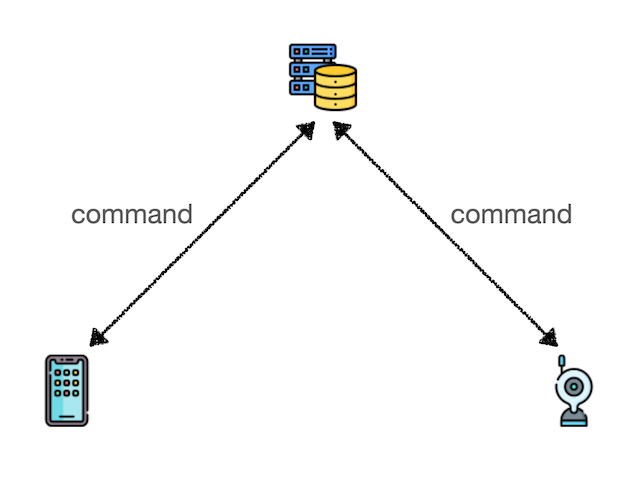
Advantages:
- Server control and monitoring
- Quick deployment
- Centralized maintenance
Disadvantages:
- System failure if server goes down
- High server/bandwidth rental costs
- Privacy concerns with data passing through servers
Distributed Control Approach

Advantages:
- No server dependency
- No rental fees
- Direct device communication
Disadvantages:
- Complex programming requirements
- Difficult app/firmware updates
- Frequent disconnections requiring reconnection
Key Question: If the server doesn’t participate, how do mobile devices and IP cameras communicate directly in a distributed architecture?
This is the core focus of this article - P2P + NAT Traversal technology.
🔗 What is P2P (Peer-to-Peer)?
P2P is a “decentralized” architecture where each device acts as both client and server. Devices can access and share resources with each other without relying on intermediary nodes.
P2P Characteristics:
- Equal peers - No hierarchy between devices
- Resource sharing - Direct file, data, or service sharing
- Scalability - Network grows with each new peer
- Resilience - No single point of failure
🌐 Understanding IPv4 and NAT
IPv4 Fundamentals
IPv4 is the foundation of the internet - every device needs a unique IP address (like a postal address) to connect online. However, IPv4 only provides approximately 4.3 billion addresses, which is insufficient for modern needs, leading to the development of NAT as an alternative solution.
IPv4 Address Structure
IPv4 Address: 192.168.1.100
│ │ │ │
│ │ │ └── Host ID
│ │ └──── Subnet
│ └──────── Network
└──────────── Class
Private vs Public IP Addresses
| Type | Range | Usage |
|---|---|---|
| Private | 10.0.0.0/8, 172.16.0.0/12, 192.168.0.0/16 | Internal networks |
| Public | All other ranges | Internet routing |
🔄 NAT (Network Address Translation)
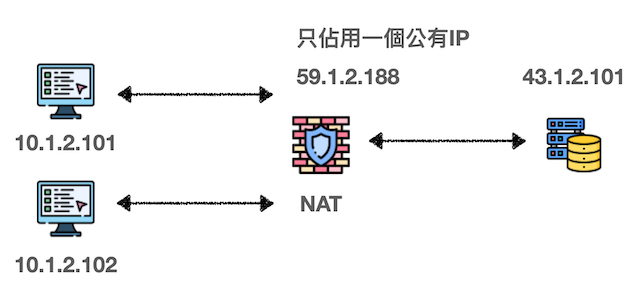
NAT allows multiple devices to share a single public IP address. It works by mapping internal IP addresses to external IP addresses, conserving IP usage. However, this creates a critical problem: external devices cannot actively connect to internal devices, which is the biggest obstacle for P2P communication.
How NAT Works:
- Internal device sends packet to external server
- NAT router replaces internal IP with public IP
- Router maintains mapping table for return traffic
- External responses are routed back to internal device
NAT Mapping Table Example:
| Internal IP:Port | External IP:Port | Protocol |
|---|---|---|
| 192.168.1.100:5000 | 203.0.113.1:12345 | TCP |
| 192.168.1.101:6000 | 203.0.113.1:12346 | UDP |
🎯 Establishing P2P Connections Through NAT
The following diagram illustrates the logical flow of NAT traversal when both parties are behind NAT:
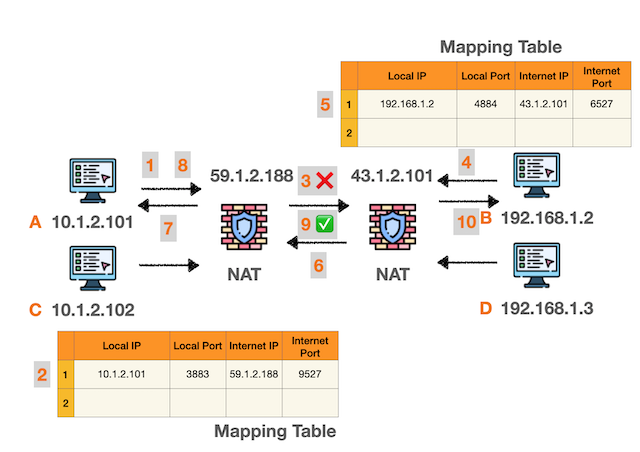
Step-by-Step NAT Traversal Process:
- Device A sends packet → Creates mapping in A’s NAT
- A’s packet blocked by B’s NAT → Connection fails
- Device B sends packet → Creates mapping in B’s NAT
- B’s packet passes through A’s NAT → Connection succeeds
- Both NATs have mappings → Bidirectional P2P established
Key Requirements for Success:
- Timing coordination between devices
- Compatible NAT types on both sides
- Proper hole-punching sequence
- Fallback mechanisms for failures
📊 Common NAT Types Analysis
Understanding different NAT types is crucial for successful P2P implementation.
✅ Full Cone NAT (Most P2P-Friendly)
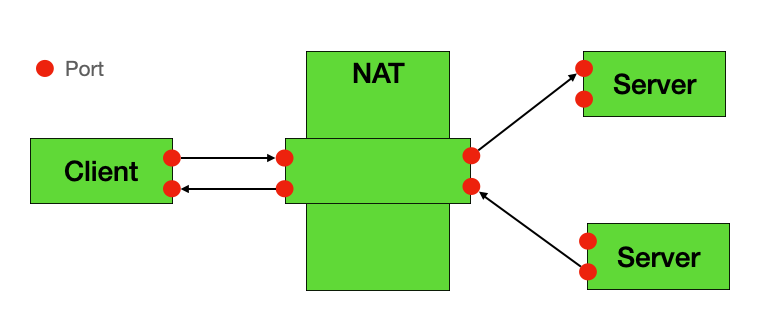
Characteristics:
- Any external host can communicate with internal device
- Most P2P-friendly NAT type
- Easiest to traverse
Behavior:
- Once internal device sends packet, external host can send to any port
- No restrictions on source IP or port
💡 Development Tip: If you can’t determine user NAT types during development, default to optimizing for Full Cone NAT. You can use STUN servers to report NAT properties.
🟡 Restricted Cone NAT
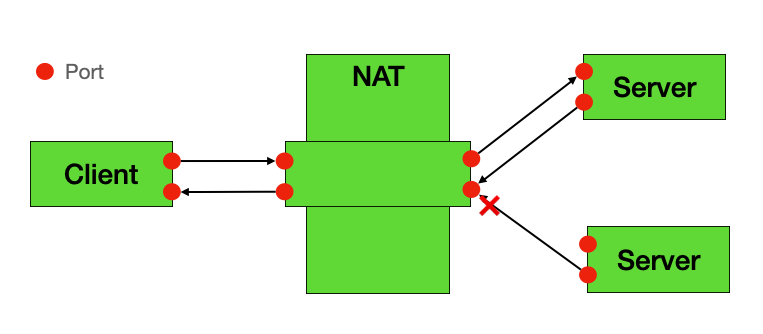
Characteristics:
- Only external hosts that internal device has contacted can send packets back
- Acceptable for P2P, but requires outbound traffic to establish mapping
Behavior:
- External host must have been contacted by internal device first
- Port restrictions may apply
🟠 Port Restricted Cone NAT
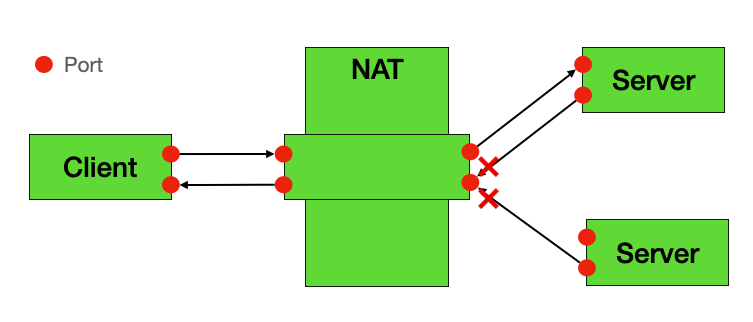
Characteristics:
- Similar to Restricted Cone, but requires exact port matching
- Higher difficulty for traversal
Behavior:
- External host must use same port that internal device contacted
- More restrictive than Restricted Cone
🔴 Symmetric NAT (Most Challenging)
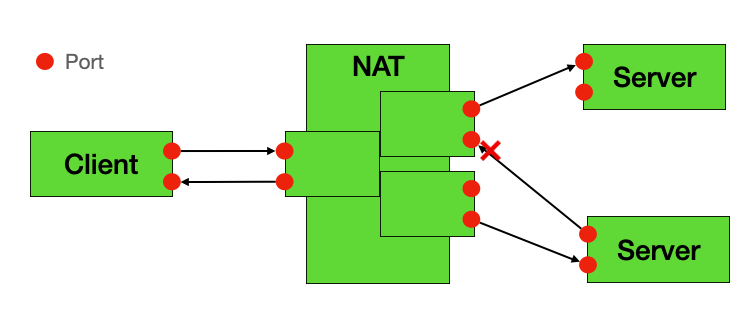
Characteristics:
- Different external port for each destination
- Almost impossible to traverse directly
- Requires TURN server as relay
⚠️ Warning: Symmetric NAT is nearly impossible to traverse directly. You need to combine with TURN servers as relays, otherwise the mapping tables on both sides cannot establish connectivity.
🛠️ NAT Traversal Techniques
1. STUN (Session Traversal Utilities for NAT)
- Purpose: Discover NAT type and external IP
- Use case: Full Cone and Restricted Cone NATs
- Limitation: Doesn’t work with Symmetric NAT
2. TURN (Traversal Using Relays around NAT)
- Purpose: Relay traffic when direct connection fails
- Use case: Symmetric NAT or when STUN fails
- Trade-off: Higher latency and server costs
3. ICE (Interactive Connectivity Establishment)
- Purpose: Framework combining STUN and TURN
- Use case: WebRTC and modern P2P applications
- Advantage: Automatic selection of best connection method
📈 Real-World Applications
IoT Device Communication
- Smart home devices connecting directly
- IP cameras streaming to mobile apps
- Sensor networks sharing data
Gaming and Entertainment
- Multiplayer games with direct connections
- Video streaming between devices
- File sharing applications
Business Applications
- Video conferencing without central servers
- Collaborative tools with direct file sharing
- Distributed computing networks
🚨 Common Challenges and Solutions
Challenge: NAT Type Detection
Problem: Determining client NAT type for optimal traversal Solution: Use STUN servers to analyze NAT behavior
Challenge: Connection Reliability
Problem: Frequent disconnections in P2P networks Solution: Implement automatic reconnection and fallback mechanisms
Challenge: Security Concerns
Problem: Direct connections may bypass security measures Solution: Implement end-to-end encryption and authentication
🔗 Related Articles
- STUN and TURN Protocol Deep Dive
- WebRTC and Key-Value Store Implementation
- Network Packet Analysis on Android
- iOS Network Packet Capture
✅ Conclusion
P2P architecture and NAT types are fundamental underlying cores for IoT device communication that cannot be ignored. Understanding connection behavior in different scenarios is the first step toward ensuring stability and scalability.
Key Takeaways:
- 🌐 NAT types significantly impact P2P success rates
- 🔧 Proper traversal techniques are essential for direct connections
- 📱 IoT applications benefit greatly from P2P technology
- 🛡️ Security and reliability must be considered in P2P implementations
Next Steps:
- Test your NAT type using online tools
- Implement STUN/TURN for robust P2P connections
- Consider WebRTC for modern P2P applications
- Plan fallback mechanisms for connection failures
💡 Pro Tip: Start with STUN for NAT discovery, then implement TURN as a fallback for challenging NAT types.
🔔 Stay Updated: Follow our P2P technology series for more advanced networking insights!
📚 Additional Resources:
Enjoy Reading This Article?
Here are some more articles you might like to read next: