STUN, TURN, and ICE: Complete Guide to NAT Traversal Protocols
🚀 Introduction to NAT Traversal Protocols
In our previous article, we discussed centralized, decentralized, and distributed network architectures, along with IPv4, NAT, and their traversal challenges. However, several critical questions remain unanswered:
- ✅ How do devices A and B discover each other’s internal/external IP addresses? (STUN)
- ✅ What happens when encountering Symmetric NAT? (TURN)
- ✅ Is there a framework that integrates the entire NAT traversal process? (ICE)
This article will help you understand these three key technologies that make P2P communication possible.
What You’ll Learn:
- 🌐 STUN protocol for NAT discovery and type detection
- 🔄 TURN protocol for relay-based communication
- ⚡ ICE framework for intelligent connection establishment
- 🛠️ Real-world implementation strategies
🌐 STUN (Session Traversal Utilities for NAT)
What is STUN?
STUN is a protocol that allows devices behind NAT to discover their public IP address, port, and NAT type. Think of it as a mirror that shows you “how the outside world sees you.”
Key Characteristics:
- RFC Definition: RFC 5389
- Purpose: NAT discovery and type detection
- Method: Client-server communication
- Limitation: Cannot handle Symmetric NAT
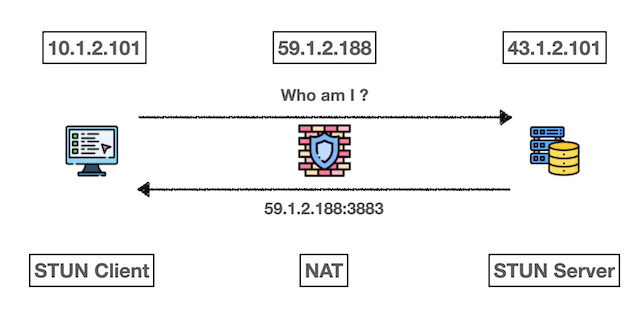
How STUN Works:
- Client sends request to STUN server
- Server responds with client’s public IP and port
- Client learns its external network identity
- Peers exchange public addresses for direct connection
STUN Message Flow:
Client STUN Server
| |
|---- STUN Request ------>|
| |
|<--- STUN Response ------|
| (Public IP:Port) |
STUN Benefits:
- ✅ Free and open - No licensing costs
- ✅ Low latency - Direct P2P connection possible
- ✅ Scalable - Minimal server resources required
- ✅ Standard protocol - Widely supported
💡 Pro Tip: STUN is the essential first step for P2P communication, but it becomes ineffective when dealing with Symmetric NAT.
🔄 TURN (Traversal Using Relay NAT)
What is TURN?
TURN is a “relay protocol” that comes into play when STUN hole-punching fails (e.g., when encountering Symmetric NAT). It acts as a communication intermediary.
Key Characteristics:
- Purpose: Relay-based communication when direct connection fails
- Method: Server-mediated data transfer
- Use case: Symmetric NAT or strict firewall environments
- Trade-off: Higher latency and bandwidth costs
TURN Operation Logic:
- Client requests relay connection from TURN server
- Server allocates relay port for the client
- All data flows through TURN server
- Server forwards data between clients
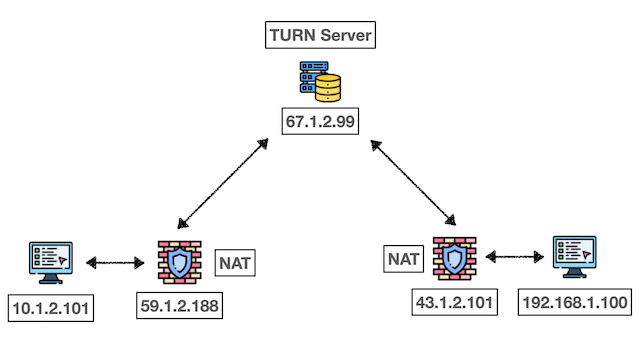
TURN Message Flow:
Client A TURN Server Client B
| | |
|---- Allocate Request ---->| |
|<--- Allocate Response ----| |
| | |
|---- Send Data ----------->| |
| |---- Forward Data ----------->|
| |<--- Send Data ---------------|
|<--- Forward Data ---------| |
TURN Considerations:
| Aspect | Impact |
|---|---|
| Latency | Higher due to relay routing |
| Bandwidth | Double consumption (client-server-client) |
| Cost | Server infrastructure required |
| Reliability | High (server-mediated) |
| Privacy | Data passes through third-party server |
⚠️ Warning: TURN solves connectivity issues but routes all data through the TURN server, increasing bandwidth costs and latency. Commercial services typically require deploying their own TURN servers.
⚡ ICE (Interactive Connectivity Establishment)
What is ICE?
ICE is a comprehensive NAT traversal framework that integrates STUN, TURN, and other protocols to make communication processes more intelligent.
Key Characteristics:
- Purpose: Intelligent connection establishment
- Method: Multi-protocol integration
- Approach: Automatic fallback mechanism
- Standard: RFC 5245
ICE Operation Logic:
- Gather candidates from all available methods (STUN, TURN, local)
- Prioritize connection candidates
- Test connectivity between all candidate pairs
- Select optimal connection path
- Establish connection using best available method
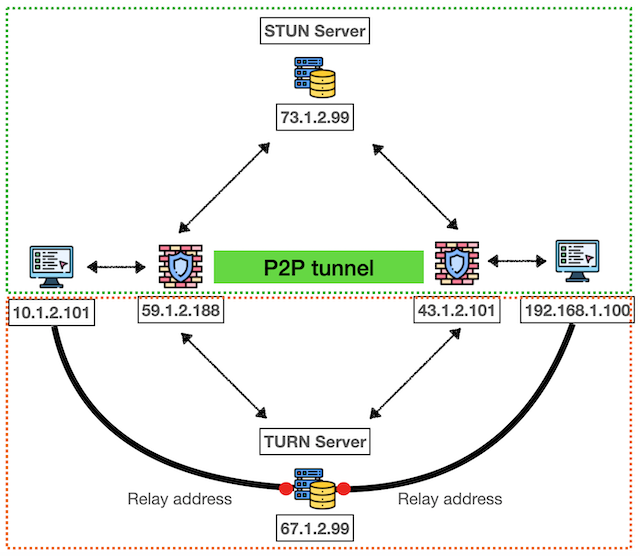
ICE Candidate Types:
| Candidate Type | Description | Priority |
|---|---|---|
| Host | Local network address | Highest |
| Server Reflexive | STUN-discovered public address | High |
| Relay | TURN server relay address | Medium |
| Peer Reflexive | Discovered during connectivity checks | Variable |
ICE Connectivity Check Process:
Phase 1: Candidate Gathering
├── Host candidates (local IPs)
├── Server reflexive candidates (STUN)
└── Relay candidates (TURN)
Phase 2: Connectivity Checks
├── Test all candidate pairs
├── Measure latency and bandwidth
└── Validate connectivity
Phase 3: Connection Establishment
├── Select optimal candidate pair
├── Establish connection
└── Begin data transfer
💡 Pro Tip: ICE is the mainstream approach for modern P2P communication. WebRTC, Zoom, Google Meet, and other real-time communication platforms all incorporate ICE mechanisms for NAT traversal.
📊 Protocol Comparison and Selection
Protocol Comparison Table:
| Protocol | Purpose | Use Case | Latency | Cost | Complexity |
|---|---|---|---|---|---|
| STUN | NAT discovery | Direct P2P connection | Low | Free | Simple |
| TURN | Relay communication | Symmetric NAT | High | Paid | Medium |
| ICE | Framework integration | Complete solution | Variable | Variable | Complex |
When to Use Each Protocol:
STUN Only:
- ✅ Simple NAT environments (Full Cone, Restricted Cone)
- ✅ Low-latency requirements
- ✅ Cost-sensitive applications
- ✅ Basic P2P communication
TURN Only:
- ✅ Symmetric NAT environments
- ✅ Strict firewall restrictions
- ✅ Reliability over performance
- ✅ Enterprise applications
ICE Framework:
- ✅ Production applications
- ✅ Multiple NAT types support
- ✅ Automatic fallback requirements
- ✅ WebRTC implementations
🛠️ Implementation Strategies
1. STUN Implementation
// WebRTC STUN configuration
const configuration = {
iceServers: [
{
urls: "stun:stun.l.google.com:19302",
},
],
};
const peerConnection = new RTCPeerConnection(configuration);
2. TURN Implementation
// WebRTC TURN configuration
const configuration = {
iceServers: [
{
urls: "turn:your-turn-server.com:3478",
username: "username",
credential: "password",
},
],
};
3. ICE Implementation
// Complete ICE configuration
const configuration = {
iceServers: [
// STUN servers
{ urls: "stun:stun.l.google.com:19302" },
{ urls: "stun:stun1.l.google.com:19302" },
// TURN servers
{
urls: "turn:your-turn-server.com:3478",
username: "username",
credential: "password",
},
],
iceCandidatePoolSize: 10,
};
🚨 Common Challenges and Solutions
Challenge 1: Symmetric NAT Detection
Problem: STUN fails with Symmetric NAT Solution: Implement TURN fallback mechanism
Challenge 2: Firewall Restrictions
Problem: Corporate firewalls block P2P traffic Solution: Use TURN servers with enterprise-grade infrastructure
Challenge 3: Connection Reliability
Problem: Intermittent connection failures Solution: Implement ICE with multiple candidate gathering
Challenge 4: Performance Optimization
Problem: High latency with TURN relay Solution: Deploy geographically distributed TURN servers
📈 Real-World Applications
1. WebRTC Applications
- Video conferencing platforms
- Peer-to-peer file sharing
- Real-time gaming
- Collaborative tools
2. IoT Device Communication
- Smart home devices
- Industrial sensors
- Connected vehicles
- Remote monitoring systems
3. Mobile Applications
- Voice and video calling
- Real-time messaging
- Location-based services
- Content sharing
🔗 Related Articles
- P2P Technology Fundamentals
- WebRTC and Key-Value Store Implementation
- Network Packet Analysis on Android
- iOS Network Packet Capture
✅ Conclusion
The three protocols play the following roles in NAT traversal:
| Protocol | Function Description |
|---|---|
| STUN | Helps you discover “how you appear to the external network” |
| TURN | Provides relay communication when hole-punching fails |
| ICE | Selects the best communication method with automatic fallback |
Key Takeaways:
- 🌐 STUN is essential for NAT discovery but limited with Symmetric NAT
- 🔄 TURN provides reliable relay communication at the cost of performance
- ⚡ ICE integrates both protocols for optimal connection establishment
- 🛠️ Implementation should consider NAT types and application requirements
Best Practices:
- Always implement ICE for production applications
- Deploy multiple STUN servers for redundancy
- Use TURN as fallback for challenging NAT environments
- Monitor connection quality and optimize accordingly
💡 Pro Tip: For all real-time video/device connection services, implement the ICE framework to maximize connection success rates while maintaining STUN/TURN backup mechanisms.
💡 Pro Tip: Consider using multiple STUN servers from different providers to improve reliability and reduce dependency on single services.
🔔 Stay Updated: Follow our P2P technology series for more advanced networking insights!
📚 Additional Resources:
Enjoy Reading This Article?
Here are some more articles you might like to read next: